One of the biggest limitations of Hyper-V in Windows Server 2008 R2 was that it didn’t support storing a Virtual Hard Disk (VHD) on physical disks larger than 2 TB. This was actually due to the sector size of the physical disk which was supported by Hyper-V. Larger disks tended to use 4096-byte sectors (also known as 4k sectors). Continue reading
Tag: Microsoft
Permanent link to this article: https://www.robertborges.us/2013/03/windows/windows-server-2012/windows-server-2012-new-feature-large-disk-support-for-hyper-v/
Windows Server 2012 New Feature: Store Hyper-V VHDs in a SMB 3.0 Share
Permanent link to this article: https://www.robertborges.us/2013/03/windows/windows-server-2012/windows-server-2012-new-feature-store-hyper-v-vhds-in-a-smb-3-0-share/
Should I Purchase Windows 7 or Windows 8
It depends…
Whether you are buying a new PC or thinking of upgrading an existing PC, the choice of Windows 7 or Windows 8 is not an easy one. To determine whether Windows 8 will work for you and your environment you first have to consider: application compatibility, added benefits, and usability. Once you have done that you can then determine which edition of Windows you should purchase (Windows 8 Core, Pro, Enterprise, or Windows RT). Continue reading
Permanent link to this article: https://www.robertborges.us/2012/12/questions-answers/should-i-purchase-windows-7-or-windows-8/
Using SYSPREP Before Creating a System Image
SYSPREP is a Windows utility that allows a computer to be generalized. If you’re restoring system images (using Ghost or a similar technology) to multiple PCs on a network, then it is imperitive that you first run SYSPREP to generalize the system.
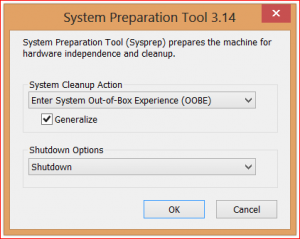
Not doing this will not only result in several PCs with the same computer name, but their unique identifiers (used by Active Directory and others) will all be identical. As you can imagine, having multiple PCs with the same computer name can be a real issue for network admins. Running a
SYSPREP allows the PC to be generalized with new unique IDs so that you get an “Out of the Box” experience (OOBE) on the next boot. While a SYSPREP can be done to any PC before attaching it to the network, I suggest running SYSPREP before you create a master image.
How to SYSPREP a Windows 7 or Windows 8 PC:
- Browse to “C:\Windows\System32\Sysprep” folder and launch the SYSPREP executable.
- In the System Cleanup Action drop down select “Enter System Out of Box Experience (OOBE)”
- Make sure to check the Generalize checkbox
- In the Shutdown options I suggest selecting Shutdown. This way after the system is prepped, the PC will shutdown, and will be ready for you to create your master image.
Once your system has gone through the SYSPREP process, before the computer boots again, it is safe to create a master image using your imaging software.
This method works not only on Windows 7, but Windows 8 and Windows Server 2008 and Windows Server 2012. I do also want to mention that it is a good idea to run SYSPREP on any virtual guest templates before rolling them out in masses on a Hyper-V or VMware host.
Related Posts:
Permanent link to this article: https://www.robertborges.us/2012/12/windows/using-sysprep-before-creating-a-system-image/
Free ebook: Introducing Windows 8: An Overview for IT Professionals
 Microsoft Press has released the final edition of Introducing Windows 8: An Overview for IT Professionals. This book covers topics such as Windows 8 deployment, security system recovery, delivering Windows apps, management, IE 10, and of course virtualization using Hyper-V for Windows 8.
Microsoft Press has released the final edition of Introducing Windows 8: An Overview for IT Professionals. This book covers topics such as Windows 8 deployment, security system recovery, delivering Windows apps, management, IE 10, and of course virtualization using Hyper-V for Windows 8.
This eBook is available in PDF (Adobe Reader), MOBI (Kindle), and ePub formats. You can download the book from the Microsoft Press MSDN Blog.
Thank you Microsoft for another free eBook!
Permanent link to this article: https://www.robertborges.us/2012/11/learning-resources/free-ebook-introducing-windows-8-an-overview-for-it-professionals/
Introducing Hyper-V Quick Migration
In the Hyper-V world, lots of us talk about Live Migration. That is where a virtual machine (VM) is moved from one host to another with no perceived downtime. The caveat is that both hosts need be configured to use the same shared storage (such as a SAN or external drive array). Continue reading
Permanent link to this article: https://www.robertborges.us/2012/07/windows/windows-server-2008-r2/hyper-v-quick-migration/
What printers work best with a Windows Remote Desktop Server?
In the Windows 2003/Windows XP days, printing on a Remote Desktop server was limited to those servers who have drivers for that particular server. Drivers for any locally attached printers would not only have to be installed on the PC that they were attached to, but also on the server you were remotely connecting to.
Now with Windows 2008 R2, Remote Desktop users have the ability to use printer redirection using Microsoft’s EasyPrint. Basically EasyPrint is part of Windows Server, and allows print jobs in a Remote Desktop session to be sent to the client for print job handling, instead of trying to print the job itself. While this is slightly slower than the old method, it allows for a much larger number of compatible printers without the need of installing drivers on the server.
Which printers will work? Well most printers that work with Windows 7 will work with Microsoft’s EasyPrint technology. If you are planning on purchasing a new printer and want to ensure that it will be fully compatible with any Remote Desktop servers you are connecting to, then check out Microsoft’s Windows Catalog database.
Any new printer you are considering should be certified for Windows 2008 R2 to fully ensure it will work well with a Remote Desktop server.
Permanent link to this article: https://www.robertborges.us/2012/06/windows/what-printers-work-best-with-a-windows-remote-desktop-server/
What to do when a print job crashes your printer spooler service
Often times printers do not work the way we expect them to. Sometimes when print jobs get stuck in the queue or cause the Windows printer spooler service to crash we need to step in to help. Here are a few quick steps that will take care of most scenarios that a simple reboot won’t fix.
On a side note, it is usually best if your computer is running the latest driver software from your printer’s manufacturer. This can generally be downloaded from the manufacturer’s website.
- Disconnect the printer from the PC. As long as Windows sees the printer connected it will try to print any jobs in the printer’s queue, including the job causing the problem. You can accomplish this by unplugging the printer’s data cable (usually USB) from either the back of the computer or from the back of the printer.
- Restart the Print Spooler service. Open a command prompt (with admin rights if using Windows 7) and type the following command followed by the <Enter> key:
net stop spooler & net start spooler
The spooler service should restart and bring you back to the command prompt.
NOTE: For more on this step, see my post on How to Open the Command Prompt with Admin Rights. - Open the printer’s queue and delete any stuck jobs.
- Reconnect the printer to the PC. Windows will reconnect the printer and make it available. Try printing a test page to make sure it is working OK.
Related Posts:
Permanent link to this article: https://www.robertborges.us/2012/06/windows/what-to-do-when-a-print-job-crashes-your-printer-spooler-service/
How to open the Command Prompt in Windows 7/Vista with Administrative Rights
In Windows XP all programs were run with administrator rights if you were logged in to the computer with a user account with admin rights to that system. There are obviously some security concerns with this, as any piece of software can potentially do damage to your system. This all changes with Windows Vista and Windows 7 as long as you keep UAC (User Access Control) enabled. UAC prevents software that need to access certain parts of Windows from running without any checks and balances.
By default, all programs are run without administrative rights. There are some cases where it is necessary to escalate the rights of an application so that it runs with these admin rights. A good example of this is Windows’ built-in Command Prompt utility. If you launch the Windows Command Prompt from the Start Menu, it will run with normal user (not administrative) rights. When the Command Prompt is opened this way, you will be allowed to do things like run a directory search or copy files, but not more advanced functions such as restarting Windows services. To allow these commands to run, you’ll first need to open the Command Prompt with administrative rights.
Opening the Command Prompt in Windows 7 with Administrative Rights:
- Click on the Start Menu and browse for the command prompt (Start >> All Programs >> Accessories >> Command Prompt), or search for Command Prompt.
- Instead of clicking on the Command Prompt icon to open it, right-click and select Run as Administrator.
- You may get prompted to allow this action, if you do simply click on the Yes button.
Permanent link to this article: https://www.robertborges.us/2012/06/windows/how-to-open-the-command-prompt-in-windows-7vista-with-administrative-rights/
How to remotely access you home or office PC
There is no shortage to the number of methods one can use to remotely access another computer. Now I’m not talking about any kind of Spyware, but rather remote control software or services which are perfectly safe, legal, and on the up and up. Continue reading
Continue reading
Permanent link to this article: https://www.robertborges.us/2012/05/mobile-computing/how-to-remotely-access-you-home-or-office-pc-2/
Using BitLocker to Encrypt Computers without TPM Hardware
It is very common for laptops to be lost or stolen. When this happens any data on the laptop could fall into the wrong hands. That is unless you have encrypted your device using BitLocker or another drive encryption technology.
If you’re not already familiar with it, BitLocker is the drive encryption technology introduced with Windows Vista and Windows Server 2008. The latest version has increased functionality and security. BitLocker is now available with Windows 7 Enterprise, Windows 7 Ultimate, and some editions of Windows Server 2008 R2.
By default BitLocker requires that your computer have a TPM chip built-in. This is a secure component which can securely keep your encryption key information. But what if you don’t have a TPM chip built-in to your computer? Continue reading
Permanent link to this article: https://www.robertborges.us/2012/05/windows/using-bitlocker-to-encrypt-computers-without-tpm-hardware/
Recovering from a Spyware or Virus Infection
In my previous post (Preventing Spyware or Virus Infections) I explained how to help protect yourself from virus and spyware infections. If you still do contract a spyware or virus infection, there are a few things you can do to clean up your PC or laptop. Continue reading
Permanent link to this article: https://www.robertborges.us/2012/05/it-security/recovering-from-a-spyware-or-virus-infection/
Preventing Spyware or Virus Infections
The best way to fight malware or viruses is to prevent them from infecting your computer in the first place. You can help keep your computer protected by: Continue reading
Permanent link to this article: https://www.robertborges.us/2012/04/it-security/preventing-spyware-or-virus-infections/
Easy Steps to Increase your Computer’s Performance
 As you may have noticed, even the fastest computers tend to get slower as they age. These performance issues could be because either the hardware is no longer sufficient for the programs now running on it, or because it needs a little maintenance. Here are a few steps you can take to help speed up your system. Continue reading
As you may have noticed, even the fastest computers tend to get slower as they age. These performance issues could be because either the hardware is no longer sufficient for the programs now running on it, or because it needs a little maintenance. Here are a few steps you can take to help speed up your system. Continue reading
Permanent link to this article: https://www.robertborges.us/2012/04/windows/easy-steps-to-increase-your-computers-performance/
Tech Update 2012 – FREE Event on Wednesday May 2, 2012
IT Pro Tech Update 2012
On Wednesday May 2nd 2012, the IT-Pro User Group is hosting Tech Update 2012 an all day FREE event. Come join us for this FREE event and discover the next phase of Information Technology as we discuss Windows 8 in the business environment, Virtualization, Security, Interoperability, and Systems Management. Here is your chance to learn what the impact of Windows 8 server and desktop will have and how you can leverage them to your advantage. We all know that Virtualization is huge but are you sure your virtual machines are secure enough? Will Windows 8 make a difference in the Virtual world? How does virtualization in the cloud work? Come learn the answers to these questions and more from some of the top experts in these fields.
This is a multi-session, multi-track event so it will draw a crowd of the right people. These are primarily IT Professionals in southern New England that are interested in advancing their knowledge and use of system management, virtualization, and cloud computing in an effort to know how to move their companies forward.
Open Wi-Fi and power will be available at seats.
Register for this event online:
http://www.IT-Pro.org/event2012
Event Type: Tech Fest
Location:
1408 Division Rd.
East Greenwich, RI, 02818
Best for: Developer and IT Pro and Public Sector and Student.
Permanent link to this article: https://www.robertborges.us/2012/04/uncategorized/tech-update-2012-free-event-on-wednesday-may-2-2012/

